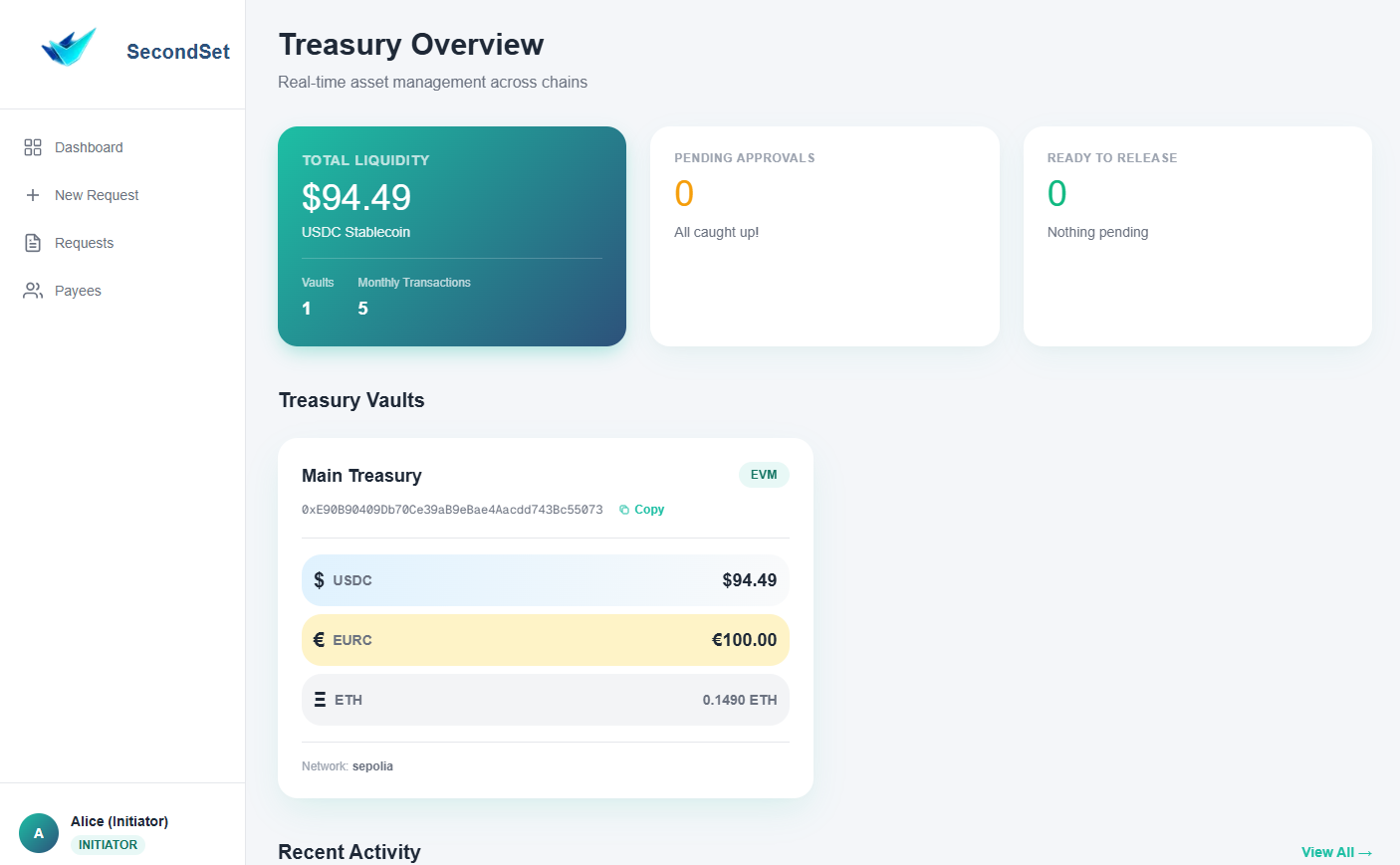
Enterprise Treasury
Secured by Your Team's Phones
Multi-signature crypto treasury with m-of-n threshold security (minimum 2). No hardware wallets. No seed phrases to lose. Just your team's mobile devices.